Routers And Switches Authentication . What is the user allowed to do? there are two general ways that authentication is implemented by most routing protocols: Verify the identity of the user. Used for billing and auditing. we currently use ise 2.2 and the radius protocol to ssh into our network gear. The idea behind aaa is that a user has to authenticate before getting access to the network. We now have a requirement to make. there are mainly two ways to authenticate to a cisco router device (and also to other networking devices in general). Radius and authentication, authorization, and accounting (aaa) must be enabled to use any of the configuration. What resources can he/she access?
from pediaa.com
there are two general ways that authentication is implemented by most routing protocols: we currently use ise 2.2 and the radius protocol to ssh into our network gear. Verify the identity of the user. The idea behind aaa is that a user has to authenticate before getting access to the network. Radius and authentication, authorization, and accounting (aaa) must be enabled to use any of the configuration. Used for billing and auditing. there are mainly two ways to authenticate to a cisco router device (and also to other networking devices in general). We now have a requirement to make. What is the user allowed to do? What resources can he/she access?
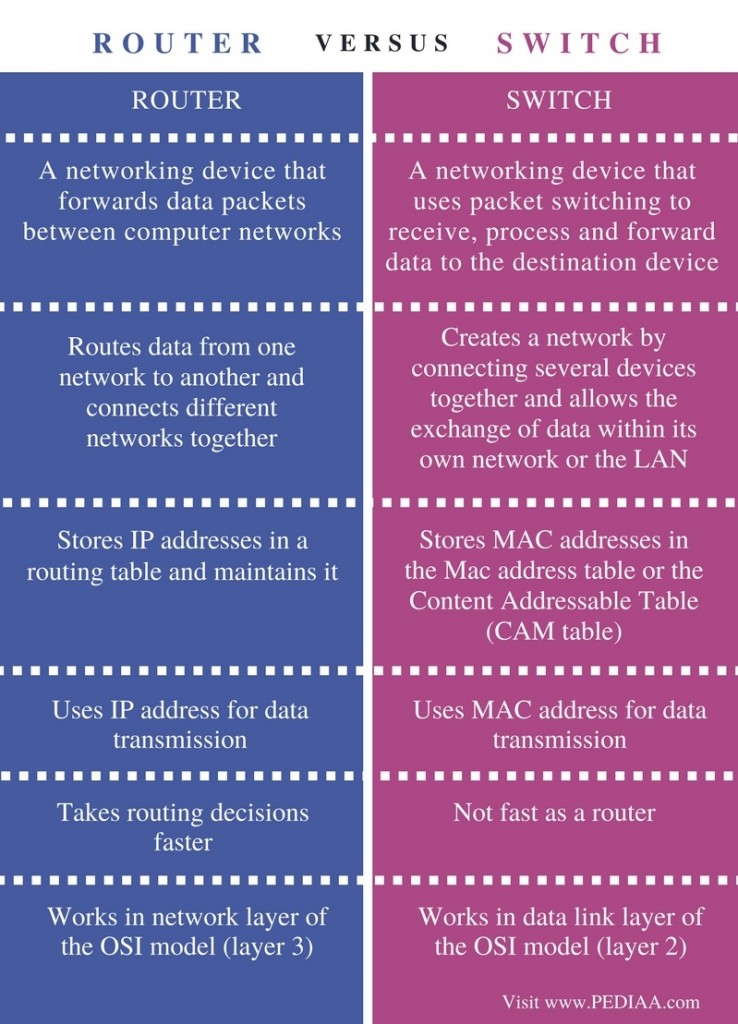
Difference Between Router and Switch
Routers And Switches Authentication We now have a requirement to make. Radius and authentication, authorization, and accounting (aaa) must be enabled to use any of the configuration. What resources can he/she access? We now have a requirement to make. Verify the identity of the user. there are two general ways that authentication is implemented by most routing protocols: The idea behind aaa is that a user has to authenticate before getting access to the network. there are mainly two ways to authenticate to a cisco router device (and also to other networking devices in general). Used for billing and auditing. What is the user allowed to do? we currently use ise 2.2 and the radius protocol to ssh into our network gear.
From www.youtube.com
Configuring AAA Authentication on Cisco Routers, Packet Tracer YouTube Routers And Switches Authentication we currently use ise 2.2 and the radius protocol to ssh into our network gear. there are two general ways that authentication is implemented by most routing protocols: What resources can he/she access? What is the user allowed to do? We now have a requirement to make. Used for billing and auditing. The idea behind aaa is that. Routers And Switches Authentication.
From www.youtube.com
Cisco routers and switch identification. YouTube Routers And Switches Authentication The idea behind aaa is that a user has to authenticate before getting access to the network. What is the user allowed to do? Verify the identity of the user. Radius and authentication, authorization, and accounting (aaa) must be enabled to use any of the configuration. What resources can he/she access? there are two general ways that authentication is. Routers And Switches Authentication.
From electricalacademia.com
How to Install and Configure Routers and Switches Electrical Academia Routers And Switches Authentication there are two general ways that authentication is implemented by most routing protocols: The idea behind aaa is that a user has to authenticate before getting access to the network. there are mainly two ways to authenticate to a cisco router device (and also to other networking devices in general). Verify the identity of the user. What resources. Routers And Switches Authentication.
From www.youtube.com
3.6.1.2 Packet Tracer Configure AAA Authentication on Cisco Routers Routers And Switches Authentication Used for billing and auditing. Verify the identity of the user. We now have a requirement to make. Radius and authentication, authorization, and accounting (aaa) must be enabled to use any of the configuration. we currently use ise 2.2 and the radius protocol to ssh into our network gear. The idea behind aaa is that a user has to. Routers And Switches Authentication.
From auberginesolutions.com
Flutter Authentication & Navigation with go_router Routers And Switches Authentication We now have a requirement to make. there are mainly two ways to authenticate to a cisco router device (and also to other networking devices in general). The idea behind aaa is that a user has to authenticate before getting access to the network. What resources can he/she access? Used for billing and auditing. Verify the identity of the. Routers And Switches Authentication.
From www.cisco.com
Configuring MACBased Authentication on a Switch through the Command Routers And Switches Authentication there are two general ways that authentication is implemented by most routing protocols: What is the user allowed to do? Used for billing and auditing. we currently use ise 2.2 and the radius protocol to ssh into our network gear. The idea behind aaa is that a user has to authenticate before getting access to the network. Radius. Routers And Switches Authentication.
From chuyencu.com
Các thiết bị chuyển mạch bộ định tuyến bộ chia là thành phần nào của Routers And Switches Authentication we currently use ise 2.2 and the radius protocol to ssh into our network gear. The idea behind aaa is that a user has to authenticate before getting access to the network. Radius and authentication, authorization, and accounting (aaa) must be enabled to use any of the configuration. What is the user allowed to do? there are two. Routers And Switches Authentication.
From www.omnisecu.com
Cisco Router/Switch AAA Login Authentication configuration using Routers And Switches Authentication there are two general ways that authentication is implemented by most routing protocols: we currently use ise 2.2 and the radius protocol to ssh into our network gear. Radius and authentication, authorization, and accounting (aaa) must be enabled to use any of the configuration. there are mainly two ways to authenticate to a cisco router device (and. Routers And Switches Authentication.
From www.networkstraining.com
Security Hardening Checklist Guide for Cisco Routers/Switches in 10 Steps Routers And Switches Authentication Verify the identity of the user. Used for billing and auditing. we currently use ise 2.2 and the radius protocol to ssh into our network gear. The idea behind aaa is that a user has to authenticate before getting access to the network. What resources can he/she access? there are two general ways that authentication is implemented by. Routers And Switches Authentication.
From www.omnisecu.com
Cisco Router/Switch AAA Login Authentication configuration using Routers And Switches Authentication What is the user allowed to do? there are two general ways that authentication is implemented by most routing protocols: we currently use ise 2.2 and the radius protocol to ssh into our network gear. there are mainly two ways to authenticate to a cisco router device (and also to other networking devices in general). The idea. Routers And Switches Authentication.
From thietbimang.com
Switch và Router khác nhau như thế nào? Routers And Switches Authentication there are two general ways that authentication is implemented by most routing protocols: Used for billing and auditing. we currently use ise 2.2 and the radius protocol to ssh into our network gear. Verify the identity of the user. Radius and authentication, authorization, and accounting (aaa) must be enabled to use any of the configuration. What is the. Routers And Switches Authentication.
From pediaa.com
Difference Between Router and Switch Routers And Switches Authentication We now have a requirement to make. we currently use ise 2.2 and the radius protocol to ssh into our network gear. What is the user allowed to do? The idea behind aaa is that a user has to authenticate before getting access to the network. Verify the identity of the user. there are mainly two ways to. Routers And Switches Authentication.
From www.zacocomputer.com
Understanding Types Of Cisco Switches And Routers Zaco Routers And Switches Authentication The idea behind aaa is that a user has to authenticate before getting access to the network. What is the user allowed to do? there are two general ways that authentication is implemented by most routing protocols: We now have a requirement to make. there are mainly two ways to authenticate to a cisco router device (and also. Routers And Switches Authentication.
From www.freecodecamp.org
Network Devices How Hubs and Switches Work and How to Secure Them Routers And Switches Authentication The idea behind aaa is that a user has to authenticate before getting access to the network. Radius and authentication, authorization, and accounting (aaa) must be enabled to use any of the configuration. Used for billing and auditing. What resources can he/she access? there are mainly two ways to authenticate to a cisco router device (and also to other. Routers And Switches Authentication.
From technicalustad.com
Switch VS Router The Definitive Comparison Guide 😎🤴 Routers And Switches Authentication there are mainly two ways to authenticate to a cisco router device (and also to other networking devices in general). Used for billing and auditing. we currently use ise 2.2 and the radius protocol to ssh into our network gear. Verify the identity of the user. We now have a requirement to make. The idea behind aaa is. Routers And Switches Authentication.
From www.youtube.com
CCNA Security Lab 3.6.1.2 Configure AAA Authentication on Cisco Routers And Switches Authentication What resources can he/she access? We now have a requirement to make. we currently use ise 2.2 and the radius protocol to ssh into our network gear. What is the user allowed to do? Verify the identity of the user. Radius and authentication, authorization, and accounting (aaa) must be enabled to use any of the configuration. there are. Routers And Switches Authentication.
From www.thetechedvocate.org
What is Routing Switch? The Tech Edvocate Routers And Switches Authentication Verify the identity of the user. there are mainly two ways to authenticate to a cisco router device (and also to other networking devices in general). What is the user allowed to do? Used for billing and auditing. What resources can he/she access? The idea behind aaa is that a user has to authenticate before getting access to the. Routers And Switches Authentication.
From bpdocs.blueprism.com
Authentication Server Routers And Switches Authentication there are two general ways that authentication is implemented by most routing protocols: We now have a requirement to make. Used for billing and auditing. Verify the identity of the user. The idea behind aaa is that a user has to authenticate before getting access to the network. there are mainly two ways to authenticate to a cisco. Routers And Switches Authentication.